
VoIP vs SIP Trunking: Which Is Better For Your Business
If you are looking to switch to an internet-based phone system, understanding the key differences between Voip vs
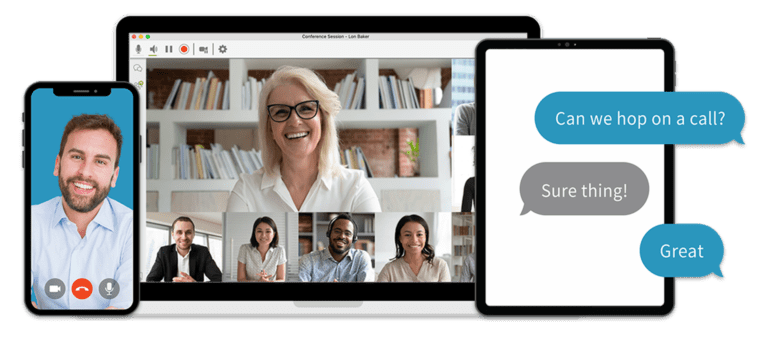

If you are looking to switch to an internet-based phone system, understanding the key differences between Voip vs

If you’re looking for a new phone number, you may want to consider getting one with the area

VirtualPBX, an award-winning business VoIP service provider, is excited to announce a new cost-effective plan and price reductions

International Women’s Day 2022 is today. And we can’t think of a better time to showcase a person

Out with the Old We have switched things up in our quest to deliver innovative customer experiences consistently.

The Season of SIP Trunking In the latest Transparency Market Research, global SIP trunking services market expects to

Navigating the Small Business Saturday 2021 Shopper Experience 2020 was a challenging year on so many levels. Especially

We have taken it to the next level in the evolution of the VirtualPBX Business Phone System. The

The last 18 months have reminded us of the true value of communication in business and connecting with

Robocalling has long been a problem in the telecom world. After years of attempting solutions like blocklists, do
Last week, we announced a new integration with Microsoft Teams, a feature customers have requested to maintain focus,
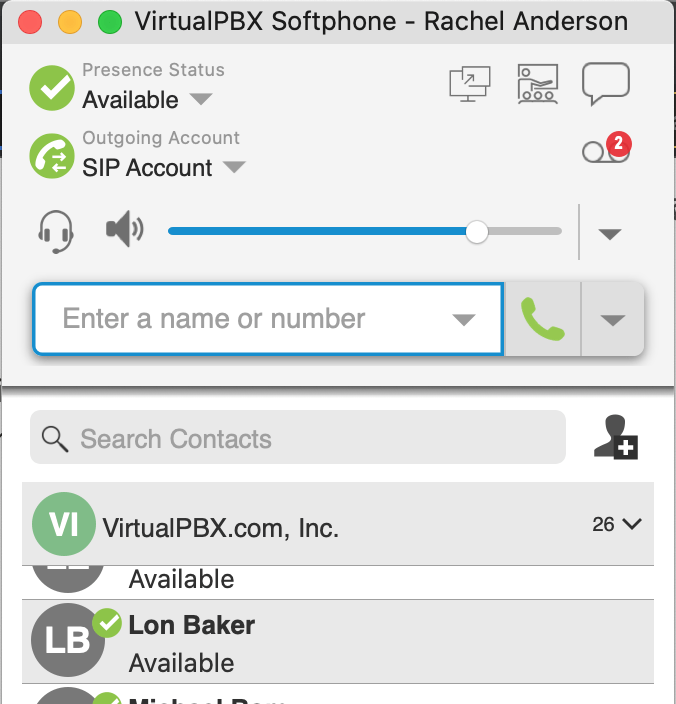
Change is one of the few constants for businesses, teams, and customers everywhere. VirtualPBX has changed tremendously over

1998-2024. VirtualPBX.com, Inc. All rights reserved. VirtualPBX, TrueACD, and ProSIP are ® trademarks of VirtualPBX.com, Inc.